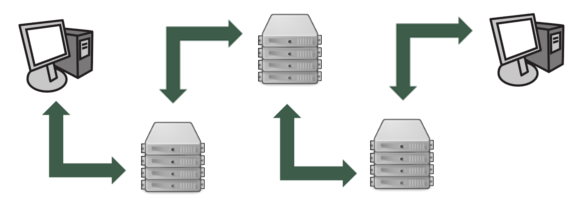
At the beginning of the use of proxy servers, in the interaction between user agents and servers, there was a single proxy server between them. Soon, several proxy servers began to appear on the path between the user agent and the source server. The reason for this was the structure of organizations using the Web. For example, a university may have a proxy server through which all Web applications run, but some university departments may have their own proxy servers. University can access the Internet through a provider, which also has its own proxy server. Finally, the outgoing server can also access the Internet through a proxy server. As a result, the user request and response of the source server pass through several proxy servers forming a chain. Currently, in the Web is quite common situation when the request passes through a group of related proxy servers. The user agent can be directly configured to communicate with the proxy server for all its Web operations.
A message from a user agent can pass through several proxy servers before it reaches the source server.
Often, the actual structure may differ from a simple linear structure. So, intermediate servers can have other servers connected to them from both sides. A fairly common structure is when a group of servers within an organization forms a hierarchy. For example, a regional proxy server may be associated with other regional proxy servers, which, in turn, may be associated with national proxy servers. Note that in this case, unlike the structure, which is a linear chain, other proxies can be located behind the regional or national proxy server. Such a hierarchical structure of proxy servers is widespread and very useful in countries where the cost of Internet access is high. By reasonably limiting the number of connections at the regional or national level, organizations can significantly reduce user latency and connection costs. A group of proxy servers can handle more caches for snoring responses. However, if there are several proxy servers, if you use the request, it becomes necessary to search for the necessary cache. In any case, you can increase your anonymity in the network by using verified proxy companies to buy proxies. proxy-seller.com has proven itself well.
The chain of proxy servers is created when you need to increase the anonymity of the Internet connection
Proxy servers know the client’s IP address. If the client is a single-user computer, or if the same value of the User-Agent field is present in user requests, the proxy server can determine that the request group originates from the same user.
Another security-sensitive information is a list of resources accessed. Selective viewing of resources accessed by the user can create a “portrait” of the user. People searching for information on certain topics related to certain diseases or visiting employment websites should, in a certain succession, take into account the risk that their problems and intentions will become known to others. In some cases, you may need Russian proxies for making chains, which can be purchased here https://proxy-seller.com/russian-proxy.
The content of the request may also contain additional information about the user, such as his birth date or his credit card number. This information is retrieved from the forms that are filled everywhere at registration for participation in conferences and mailing lists, buying goods, ordering air tickets. An obvious solution, increasingly used by many websites, is to use SSL-based encryption, in which case the proxy server is used as a tunnel. Similarly, the content of the response also carries user information.

